More Than 1600 Brands Targeted, Just By QR Code Attacks in Q2
CAMBRIDGE, MASSACHUSETTS / ACCESS Newswire / September 4, 2025 / CAMBRIDGE, Mass.-The APWG's Q2 2025 Phishing Activity Trends Report reveals increasing numbers of cybercrime attacks, with some types of phishing inflicting rapidly rising costs to the consumers and businesses they victimized during Q2 of this year.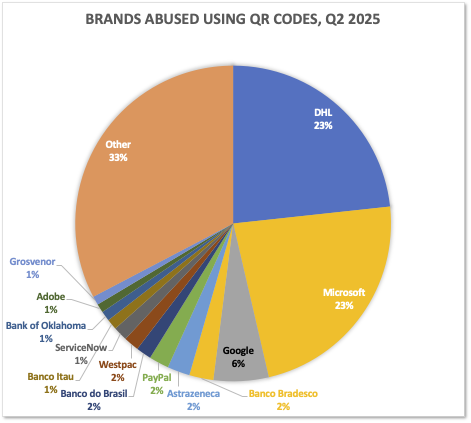
QR CODE ATTACKS IN Q2 2025
APWG will meet to consider these developments and the rise of AI as a cybercrime co-conspirator at its eCrime Symposium in November: https://apwg.org/events/ecrime2025
The number of phishing attacks has risen steadily over the last year. In the second quarter of 2025, APWG observed 1,130,393 phishing attacks, up 13 percent from 1,003,924 attacks in Q1 2025. This is the largest quarterly total since 1.28 million of these campaigns were observed in Q2 2023.
Attacks also cost companies more money in the last quarter.
"Business e-mail compromise" or BEC attacks attempt to trick employees, often key operations personnel and executives, into sending their company's money or passwords to a criminal. When criminals requested that companies send money to them via wire transfer, the average amount requested in Q2 2025 was $83,099, a 97 percent increase from Q1 2025. The total number of wire transfer BEC attacks observed also increased, by 27 percent compared to Q1 2025.
Phishers are also using the services of legitimate companies to carry out phishing.
Matthew Harris, Senior Product Manager, Fraud at Crane Authentication/OpSec Security, reported: "We are seeing a rise in the volume of phishing located on free hosting platforms, and on domains where the network and hosting infrastructure is behind third-party protection services."
APWG member Fortra documented that Green Dot was once again the preferred bank of payroll diversion scammers, with one in four payroll diversion attempts directed towards accounts at one of Green Dot's brands. Domain registrar NameCheap was used most often by BEC scammers, in almost a quarter of all BEC attacks. Google's Gmail was used for 70 percent free webmail accounts that scammers set up for BEC scams, Fortra found.
While phishers direct large numbers of attacks against certain brands (such as the U.S. Postal Service), a great many companies' brands are also being attacked. APWG contributor Mimecast found that 1,642 brands were targeted by criminals using malicious QR codes, which direct the victims to phishing sites and malware.
Report: https://docs.apwg.org/reports/apwg_trends_report_q2_2025.pdf
About APWG
The Anti-Phishing Working Group (APWG) is the global industry, law enforcement, and government coalition focused on unifying the global response to electronic crime. Membership is open to qualified financial institutions, online retailers, ISPs and Telcos, the law enforcement community, solutions providers, multilateral treaty organizations, research centers, trade associations and government agencies. SEE: APWG's apwg.org and stopthinkconnect.org websites.
Contact APWG at press@apwg.org, +1.617.669.1123). For company-specific content in this release, contact: Stefanie Wood of Crane Authentication/OpSec Security (stefanie.wood@craneauthentication.com); Jessica Ryan of Fortra (Agari and PhishLabs) (jessica.ryan@fortra.com); Tim Hamilton of Mimecast (thamilton@mimecast.com).
Contact Information
Peter Cassidy
Secretary General
pcassidy@apwg.org
617-669-1123
SOURCE: ANTI-PHISHING WORKING GROUP
View the original press release on ACCESS Newswire






